Georgia man was sentenced to over 7½ years in prison for synthetic identities scheme that defrauded banks out of nearly $2 million.
The man and his co-conspirators created “synthetic identities” by combining false personal information, such as fake names and birth dates, with real people’s data, such as social security numbers. Synthetic identities were used to open bank and credit card accounts at financial institutions.
What is synthetic identity
According to the Federal Reserve, “Synthetic identity fraud (SIF) is the use of a combination of personally identifiable information (PII) to fabricate a person or entity to commit a dishonest act for personal or financial gain.”
The two main components of synthetic identity are:
- The creation of a synthetic identity
- Using that identity to commit fraud.
Synthetic identity is often used to:
- Hide someone’s negative credit history
- Open bank accounts
- Fund the fraudster’s lifestyle
- Buy goods or services with no intent to repay
- Obtain government benefits
- Obtain medical treatment
- Commit other types of criminal activity.
- Terrorist financing
- To open “money mule” accounts.
- Etc
Where do criminals find personal information?
Criminals often steal people’s personal information through account takeovers, phishing attacks, cyberattacks, social engineering, and data breaches.
Today, with the development of technology, buying stolen information from individuals is relatively easy. The so-called “dark web” is a source that criminals are often using to buy and sell illegal products and services, including personal information of people obtained from cyberattacks.
Source: Federal Reserve Banks – https://fedpaymentsimprovement.org/synthetic-identity-fraud-mitigation-toolkit/detecting-a-synthetic-identity/
Why is synthetic identity difficult to determine?
In the U.S., banks lose billions of dollars in identity theft every year. But unfortunately, the problem is worse every year, not only in the U.S. but in many other countries worldwide.
In synthetic identity, the perpetrators are patient. They allow some time to create a good credit history with these identities and slightly increase the borrowing until they maximize their lines of credit. Then the perpetrators disappear, leaving the bank exposed.
Synthetic identity is difficult to determine because:
- Fraudsters keep their accounts for months and sometimes years with the ultimate purpose of building a reliable credit history.
- The behavior of a fraudster using a synthetic identity is very similar to the typical customer’s activity.
- Often, there is no indication of fraud until the customer maximizes the line of credit.
- Criminals are using sophisticated methods to fabricate synthetic identities that can often bypass the security systems of ID verification tools.
- Fraudsters often steal personally identifiable information of individuals who are less likely to discover the fraud, like children and homeless people.
Criminal rings use sophisticated tactics to fabricate and maintain synthetic identities and often create sham businesses and relationships with various counterparties.
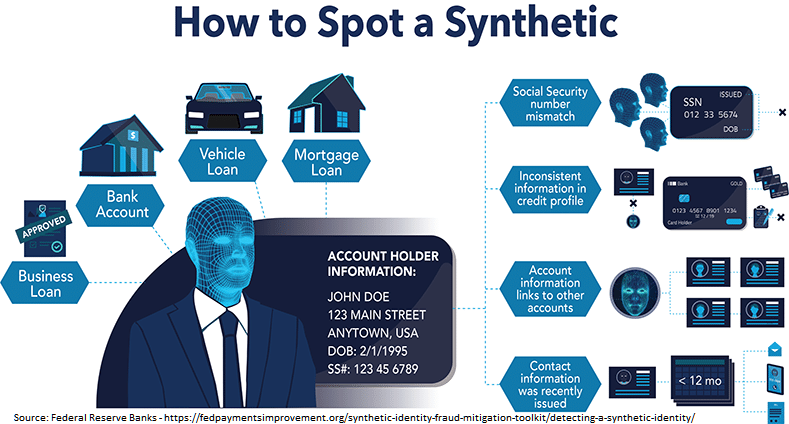
Potential indicators for synthetic identity
Although there is no single indicator for synthetic identity, combining common characteristics may raise alerts and the need for additional review. These common characteristics include:
- A large amount of unsecured debt
- A large number of credit inquiries
- A mismatch between the accountholder’s age and the duration of the credit history.
- Increase of credit line.
- Suspicious mailing address
- Recently issued contact information.
- Similar or matching contact information with other customers.
- Matching social security numbers
- Identical digital footprint.
How to protect your business from synthetic identity theft
Criminals constantly evolve, and so are their tactics. For this purpose, financial institutions must employ appropriate tools, including artificial intelligence or machine learning tools, to identify suspicious behavior, including “behavioral biometrics,” which will enable entities to spot inconsistencies in the data and obtain a holistic view of a person’s identity.



